Telerik Fiddler version 4.6 (and v2.6 targeting .NET2) is now available for download. The new version includes several new features and dozens of tweaks and bugfixes, described in this article.
View > Tabs Menu
The new View > Tabs menu offers a list of tabs that are hidden by default.
![image image]()
The Preferences command displays a tab that allows you to edit Fiddler’s Name/Value preferences.
The new APITest command displays the new Fiddler APITest tab that enables easy testing of web APIs.
The AutoSave command (formerly located in the Tools menu) permits you to automatically save Session Archive Zip files on a regular schedule.
Note: In the future, this submenu will become an extension point to allow developers to easily expose optional UI tabs.
Lint Filters
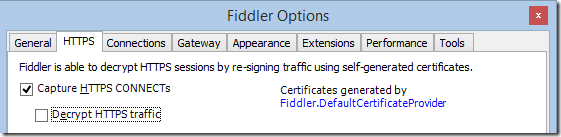
Fiddler’s Lint feature enables you to control how Fiddler reports violations of the HTTP protocol and other errors. Controlled on the Tools > Fiddler Options > General tab, you can leave the If protocol violations are observed setting at the basic “Warn on Critical errors” section or adjust it to “Warn on all errors”; the latter setting performs more tests on traffic to find mistakes that could cause clients or servers to misbehave. However, this setting can get pretty noisy. To allow you to suppress specific warnings, you can now use the Filter link on the Protocol Violation Report dialog.
![image image]()
Each Lint warning now has a unique code consisting of a letter and three digits. The letter prefix indicates the severity:
- L – Common “problem”, low impact, unlikely to break anything.
- M – Significant problem, likely to break functionality in one client.
- H – Important problem likely to significantly break functionality in multiple clients
You can exclude an entire class of warnings by simply including the prefix in the list of exclusions.
Single Session Timeline
The Timeline tab in Fiddler allows you to visualize the download of multiple Sessions at once to permit you to view parallelism and connection reuse. In Fiddler 4.6, the view of a single Session has been enhanced to permit you to visualize how the content of the Session was downloaded. You can determine, for instance, whether the headers were flushed immediately or the client was forced to wait for headers until the body was ready, and you can determine whether download speed improved or regressed as the download proceeded. For instance, in this chart, the server took 2.5 seconds to return the headers and began to slowly stream the body in small chunks. As the download progressed, the speed improved until completion at just over 9.2 seconds:
![image image]()
Interface Tweaks
A new Copy as Image command on each Inspector’s tab context menu allows you to copy an image of the tab’s contents to your clipboard for easy pasting in an email or blog post. The Headers, XML, and JSON Inspectors allow you to easily highlight nodes of interest—simply press the spacebar on a node to temporarily render it with a yellow highlight:
![image image]()
The new Math context menu appears when you right-click on a numeric column in the Web Sessions list; the menu currently offers a single command: Sum and Average, which shows these attributes of the selected Sessions:
![image image]()
The Composer tab now offers a splitter between the headers and body boxes so you can adjust their height as desired:
![image image]()
Pressing the / key while in the Web Sessions list now enters QuickSearch mode in the QuickExec box, selecting any Sessions whose URL contains the text you type.
Hash Support
Fiddler now offers enhanced support for computing hashes of blocks of bytes or strings.
The Tools > TextWizard feature now offers a quick way to get a hash (MD5 to SHA512) of a block text, in either base64 or dashed hexadecimal format:
![image image]()
New methods are also available for FiddlerScript to compute hashes. For instance, you can copy the following block to just inside your Rules > Customize Rules > Handlers class:
public BindUITab("Resource Integrity Hashes", "<nowrap><nolink>")
static function ShowSRI(arrSess: Session[]):String
{
var oSB: System.Text.StringBuilder = new System.Text.StringBuilder();
for (var i:int = 0; i<arrSess.Length; i++)
{
if (arrSess[i].HTTPMethodIs("CONNECT")) continue;
if (!arrSess[i].bHasResponse)
{
oSB.AppendFormat("\r\n// Skipping incomplete response '{0}'\r\n",
arrSess[i].fullUrl);
continue;
}
if (arrSess[i].responseCode != 200)
{
oSB.AppendFormat("\r\n// Skipping non-HTTP/200 response '{0}'\r\n",
arrSess[i].fullUrl);
continue;
}
var sType: String = arrSess[i].oResponse.MIMEType.ToLower();
var bIsScript = sType.Contains("script");
var bIsCSS = sType.Contains("css");
if (!bIsScript && !bIsCSS)
{
oSB.AppendFormat("\r\n// Skipping non-CSS/JS response '{0}'\r\n", arrSess[i].fullUrl);
continue;
}
var sIntegrity = "sha256-" + arrSess[i].GetResponseBodyHashAsBase64("sha256").Replace("-", "")
+"\n\tsha384-" + arrSess[i].GetResponseBodyHashAsBase64("sha384").Replace("-", "")
+"\n\tsha512-" + arrSess[i].GetResponseBodyHashAsBase64("sha512").Replace("-", "");
if (bIsScript)
{
oSB.AppendFormat('\r\n<script src="{0}"\r\n\tintegrity="{1}"></script>\r\n',
arrSess[i].fullUrl, sIntegrity);
}
else
{
oSB.AppendFormat('\r\n<link rel="stylesheet"\r\n\thref="{0}"\r\n\tintegrity="{1}">\r\n',
arrSess[i].fullUrl, sIntegrity);
}
}
return oSB.ToString();
}
When you save the script, Fiddler adds a new tab to display the Subresource Integrity attributes for the selected response bodies:
![image image]()
FiddlerScript Improvements
BindUITab Enhancements
As seen in the Resource Integrity Hashes example above, the BindUITab attribute allows you to create new tabs inside Fiddler that are populated based on the selected Sessions. BindUITab now offers a second parameter that allows you to specify one or more of the following options:
- <nowrap> – The RichEdit control should not wordwrap lines
- <nolink> – The RichEdit control should not detect or underline urls
- <html> – Instead of using a RichEdit control, the function’s response will be rendered as HTML inside a Web Browser Control
BeforeFiddlerShutdown event
Fiddler now exposes a BeforeFiddlerShutdown event that enables extensions or FiddlerScript to block shutdown of Fiddler; this may be useful if you wish to prompt the user for permission to lose unsaved work, etc.
A Fiddler extension should attach an event handler:
FiddlerApplication.BeforeFiddlerShutdown += (o, c) =>
{
c.Cancel = (DialogResult.Cancel ==
MessageBox.Show(“Allow Fiddler to close????”,
“Go Bye-bye?”, MessageBoxButtons.OKCancel));
};
Within FiddlerScript, you can add a method to the existing Handlers class:
static function OnBeforeShutdown(): Boolean {
return ((0 == FiddlerApplication.UI.lvSessions.TotalItemCount()) ||
(DialogResult.Yes == MessageBox.Show(“Allow Fiddler to exit?”,
“Go Bye-bye?”, MessageBoxButtons.YesNo, MessageBoxIcon.Question,
MessageBoxDefaultButton.Button2)));
}
AutoResponder Improvements
The AutoResponder now supports the NOT: operator inside the METHOD:, HEADER:, and FLAG:, operators. For instance, if you’d like the AutoResponder only to impact requests from Google Chrome, add this rule to the top of your list:
![image image]()
Microsoft Edge Support
Fiddler has been updated to recognize Microsoft’s new Edge browser as a Web Browser, so features like the Process Filter in the Status Bar:
![image image]()
…and in the Browse command in the Fiddler toolbar:
![image image]()
work as expected.
Note: You should use the WinConfig button at the left of Fiddler’s toolbar to enable Windows 10 “Store” applications to run Fiddler. By default, you shouldn’t need to use the WinConfig button for Edge, because Edge’s about:flags enables access to loopback by default.
ImageView Enhancements
FavIcon Preview
When a site uses an .ICO file as its favicon, the icon may contain multiple different images that are used depending on the user’s device and the context in which the icon is rendered. Fiddler’s ImageView Inspector now renders all of the images contained within the .ICO file like so:
![ImageView showing icon ImageView showing icon]()
JPEG Thumbnails
Websites should generally strip embedded thumbnails from JPEG files. Embedded thumbnails are a common source of bloat, wasteful bytes that aren’t used by the client. However, some sites fail to optimize their images by removing thumbnails. In some cases, an image thumbnail may even contain data which was never meant to be made public, if, for instance, the larger image was cropped without regeneration of the thumbnail. The ImageView now allows you to extract the thumbnail image as a new Session that is added to the Web Sessions list:
![Extract Thumbnail]()
AutoSave Enhancements
Fiddler’s AutoSave feature (now found under View > Tabs > AutoSave) now supports several preferences to control its behavior.
Set fiddler.extensions.AutoSave.AlwaysOn to true to have Fiddler automatically activate AutoSave mode when it starts. Set fiddler.extensions.AutoSave.Minutes to the number of minutes to collect traffic between each save operation; the default is 5. Set fiddler.extensions.AutoSave.HeadersOnly to true if you’d like the SAZ file to contain only the request and response headers, omitting the bodies. Set fiddler.extensions.AutoSave.Path to the folder path under which auto-saved SAZ files should be stored.
Additional Upgrade Notifications
By default, Fiddler’s automatic update notifications will only show if a significant change in version number occurs. For instance, say you’re running version 4.6.0.2 and version 4.6.0.3 becomes available. By default, Fiddler will only tell you about this minor update if you manually check for new versions by clicking Help > Check for Updates. When Fiddler 4.6.1.0 becomes available, the updater detects this larger change in version number and prompts you to upgrade.
If you would prefer Fiddler to notify you of every update automatically, use the black QuickExec box below Fiddler’s Web Sessions list to enter the following command:
prefs set fiddler.updater.BleedingEdge true
With this preference set, you’ll see more frequent notice of upgrades. On one hand, that’s great—you’ll get the latest Fiddler improvements ahead of most other people. On the other hand, as a bleeding edge user, you’re also more likely to uncover any bugs we inadvertently introduce in new versions.
Fiddler Improvement Program
You may now opt-in to sending telemetry information about your PC environment and Fiddler usage. Within your first few boots of Fiddler, you’ll see the following dialog:
![image image]()
Telemetry data is reported over HTTPS and its usage is governed by Telerik’s Privacy Policy. If you later change your mind, you can control your participation using the checkbox Participate in the Fiddler Improvement Program on the Tools > Fiddler Options > General tab. Note: If an administrator has set the BlockUpdateCheck registry key in the HKLM registry hive, users cannot opt-in to the Fiddler Improvement Program.
The Telerik Analytics integration into Fiddler has already yielded several bugfixes and has helped us prioritize our investments in performance and feature improvements. We’ll write more about what we’ve learned from Fiddler Telemetry in a future blog post.
Performance Improvements
One early finding from our Fiddler Telemetry is that a surprising number of users are running on 32bit Windows, where the address space limitations mean that they often run into “out of memory” errors. To help mitigate this, we’ve made some under-the-hood changes to how Fiddler allocates memory, and this is only the beginning of a larger project to improve Fiddler’s overall performance for everyone.
As a part of our performance investigations, two new commands were added to the QuickExec box, !memory and !threads. Invoke these commands to add information to the Log tab for troubleshooting purposes. If you find Fiddler is running more slowly than expected, sending the output of these commands to us will help narrow down the problem.
We hope you enjoy the new version of Fiddler!
-Eric Lawrence
![]()
![]()